Spoof: A barrier to the acceptance of Facial Recognition Systems
By Dr. Andrew O’Brien
ICU Product Manager
November 2020
The use of biometrics and facial recognition software to identify and verify individuals is being rapidly deployed and becoming commonplace across a wide range of industries. Despite some unease in terms of consumer privacy, overall, it has the potential to positivity transform our everyday lives and can bring advanced security benefits with improved accuracy, speed and contactless interaction.
Biometrics: the growth of Neural Networks
Biometrics use an individual’s unique biological characteristics to verify identity. Different biometric techniques include using fingerprints, faces, iris scanning, voice analysis and so on. Biometrics has the potential to be far more secure than the use of traditional identification techniques such as paper ID, pin numbers or RF Identification. The evolution of Artificial Intelligence (AI), in particular the growing sophistication of Neural Networks, has enabled the practical implementation of Facial Recognition across numerous applications.
The inevitable growth in the use of facial features to determine identification and estimate age requires that providers of the technology both understand and respond to the threats and attempts to spoof the technique.
A neural network is a series of algorithms that endeavours to recognise underlying relationships in a set of data through a process that mimics the way the human brain operates. In this sense, neural networks refer to systems of neurons, either organic or artificial in nature. Source: Investopedia
The importance of spoof detection
Spoofing is a type of presentation attack which tries to defeat or interfere with the biometric identification process. As biometric systems are being more widely used in real-world applications, presentation attacks or spoofs are becoming a larger threat to organisations. Fraudsters use various techniques to try and impersonate other people. For example, for facial recognition, they could hold up a photograph to try and impersonate someone or even use a video or photograph on a mobile device. More sophisticated ways to trick systems are being used such as a replay or video attack. This involves a looped video of a face which means that behaviour and facial expressions look real and not fake.
Cooperative or Intrusive Spoof:
Cooperative spoof is one of the first attempts to determine the liveness of a subject. Liveness detection is any technique used to identify a spoof attempt using algorithms to detect indicators which monitor if the person is ‘live’ or ‘fake’. This solution requires participation from the user or subject who would need to perform an action to be identified. The subject will be issued a series of random commands or prompts designed to be not easily replicated with a spoof. These instructions may be a determination of pose (look left/right/up/down) and/or emotive response (smile broadly). Their response will be monitored to determine if the subject is correctly responding to determine liveness. If the user reacts correctly then the process can proceed. If the user fails to correctly response, then a spoof alert can be raised. This approach does impact on the user experience and speed of transaction as it requires involvement, but it can be quite effective in determining spoof attempts.
In biometrics, Liveness Detection is an AI computer system’s ability to determine that it is interfacing with a physically present human being and not an inanimate spoof artifact. Source: www.liveness.com
Passive or Non-intrusive Spoof:
From a customer experience point of view non-intrusive spoof is a far more attractive option. This requires no conscious participation of the subject or user throughout the transaction. This results in a far quicker and far superior experience for the user during the transaction. However, it is a far greater challenge to implement such an approach.
ICU – Intelligent Identification
ICU is our intelligent facial recognition and age verification device which transforms a simple USB camera into a complete solution to verify authorised users/entry; automate restricted access or allow contactless handsfree entry. Utilising our own AI algorithms developed over many years, ICU offers accurate (99.88%), precise and affordable facial recognition. It is easy to integrate and simple to use. Multi-layered spoof detection constantly monitors the user in front of the camera. Our specially trained algorithms can detect photographs and videos/images on mobile devices to prevent fraud attempts. Our spoof detection is non-intrusive and takes place in the background throughout the operation without affecting the user experience. Spoof alerts can be remotely monitored and remotely overridden if determined to be a genuine transaction.
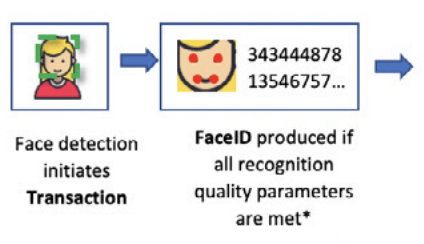
And here is the techie bit. Frames are not treated as independent events, rather they are linked together to form a ‘transaction’. Defining a transaction allows ICU to obtain dynamic information in relation to the user which in turn enhances the power of the ICU device in detecting spoof. A Transaction is defined as the period of time (> 1 frame) that a single user is detected and either an approved action is performed, a spoof is alerted and/or when the same face is no longer detected. The detailed level of data or checks that ICU undergoes when authenticating a face is outlined here:
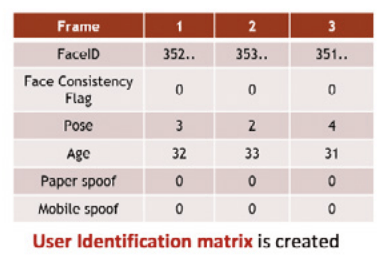
A transaction is initiated on a Face Detection event. This face is referred to as the Active face. A User Identification Matrix (UIM) is created and populated on each successive frame. Each parameter of the UIM can be utilised in conjunction with every other parameter to determine if the probability that the face is real or an attempted spoof. Our face consistency approach determines if new faces are detected and the nature of this new Imposter (spoof) face, trained algorithms are used to determine pose and other liveness indicators. We have also trained new algorithms to recognise photographs and the presentation of mobile devices. Averaging over several frames can be used to determine outlier events (where a data point that differs significantly from other observations) and reduce the occurrence of inaccurate results. Application aware processes can also be utilised to increase the efficacy of the approach. For example, in an age estimation task, if the Active face is underage and an Imposter face is overage then there is a greater weight to a potential spoof attempt. Similarly, for a exclusion event (where a particular customer is excluded from accessing a product i.e problem gamblers) if the Active face is excluded and the Imposter face is not, then again this presents as a high potential spoof. Having such an approach can aid in the cases of false positives and avoiding interrupting the customer experience to flag a spoof.
We believe that Facial Recognition and the use of the technology has the potential to have a great and positive impact on many sectors of society. Like all new technology there will be inertia to its adaptation due to many legitimate concerns such as data protection and robustness of the approach which we have covered in a previous facial recognition blog here. Legislation surrounding its proper use is necessary from Governing bodies while providers must ensure that the technology is robust and to an extent must work together to ensure that the technology is employed and distributed in a fair, open and trust worthy manner.
Sources
https://blog.innovative-technology.co.uk/facial-recognition-friend-or-foe/
https://www.aware.com/biometric-liveness-detection-spoof-detection/
https://www.liveness.com/
https://medium.com/datadriveninvestor/face-spoof-detection-e0d08fb246ea
http://cvlab.cse.msu.edu/project-face-anti.html
https://www.investopedia.com/terms/n/neuralnetwork.asp
https://rezaid.co.uk/top-5-trends-in-facial-recognition/